¶ Références
https://edu.chainguard.dev/open-source/sigstore/cosign/an-introduction-to-cosign/
¶ Articles associés
¶ Installation sur debian
sudo apt install cosign
cosign version
______ ______ _______. __ _______ .__ __.
/ | / __ \ / || | / _____|| \ | |
| ,----'| | | | | (----`| | | | __ | \| |
| | | | | | \ \ | | | | |_ | | . ` |
| `----.| `--' | .----) | | | | |__| | | |\ |
\______| \______/ |_______/ |__| \______| |__| \__|
cosign: A tool for Container Signing, Verification and Storage in an OCI registry.
GitVersion: devel
GitCommit: unknown
GitTreeState: unknown
BuildDate: unknown
GoVersion: go1.24.4
Compiler: gc
Platform: linux/amd64
¶ Signature d'une image Docker
cosign sign harbor.bv.stef.lan/library/pki-manager:latest
Generating ephemeral keys...
Retrieving signed certificate...
The sigstore service, hosted by sigstore a Series of LF Projects, LLC, is provided pursuant to the Hosted Project Tools Terms of Use, available at https://lfprojects.org/policies/hosted-project-tools-terms-of-use/.
Note that if your submission includes personal data associated with this signed artifact, it will be part of an immutable record.
This may include the email address associated with the account with which you authenticate your contractual Agreement.
This information will be used for signing this artifact and will be stored in public transparency logs and cannot be removed later, and is subject to the Immutable Record notice at https://lfprojects.org/policies/hosted-project-tools-immutable-records/.
By typing 'y', you attest that (1) you are not submitting the personal data of any other person; and (2) you understand and agree to the statement and the Agreement terms at the URLs listed above.
Are you sure you would like to continue? [y/N] y
error opening browser: exec: "xdg-open": executable file not found in $PATH
Go to the following link in a browser:
https://oauth2.sigstore.dev/auth/auth?access_type=online&client_id=sigstore&code_challenge=x1g2oFrM6k4Xruxau4TCcTcnK1ZlZJkhNKJA8K3ROB4&code_challenge_method=S256&nonce=36l7vi9MywNR0AWmap7hEVeUqDn&redirect_uri=urn%3Aietf%3Awg%3Aoauth%3A2.0%3Aoob&response_type=code&scope=openid+email&state=36l7vhrlpWYf2p50ogSRbiITKOB
Enter verification code:
Ouvrir l'url communiqué
Dans mon exemple j'ai choisi Github

Renseigner le code de vérification:
Enter verification code: xxxxxxxxxxxxx
Successfully verified SCT...
WARNING: Image reference harbor.bv.stef.lan/library/pki-manager:latest uses a tag, not a digest, to identify the image to sign.
This can lead you to sign a different image than the intended one. Please use a
digest (example.com/ubuntu@sha256:abc123...) rather than tag
(example.com/ubuntu:latest) for the input to cosign. The ability to refer to
images by tag will be removed in a future release.
tlog entry created with index: 762298928
Pushing signature to: harbor.bv.stef.lan/library/pki-manager
Dans l'exemple j'ai signé l'image taggé ( latest ) il est préférable de signer le digest.
Dans l'exemple il aurait fallu signer l'image: harbor.bv.stef.lan/library/pki-manager:v0.320d32c864f0e30e16941702117d0396a038062f car cette image est unique alors que le tag peut être mis sur une autre images à l'avenir.
¶ Vérification dans Harbor
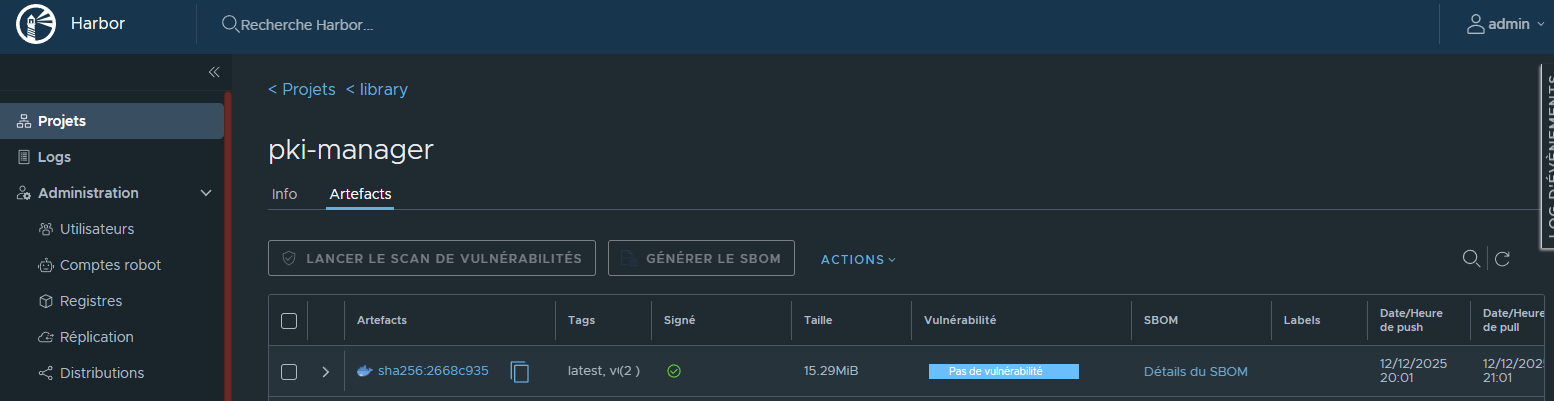
L'images est bien signée